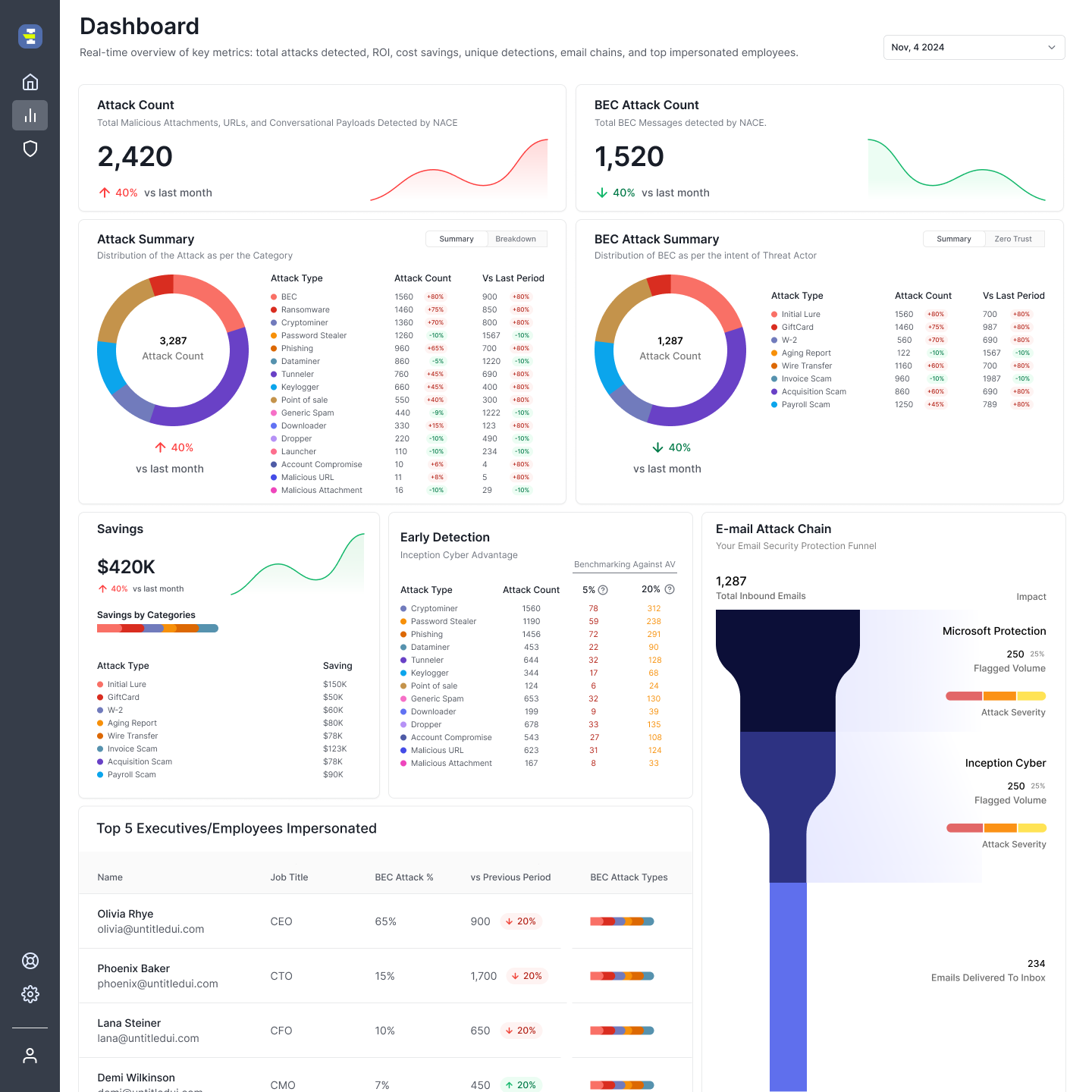

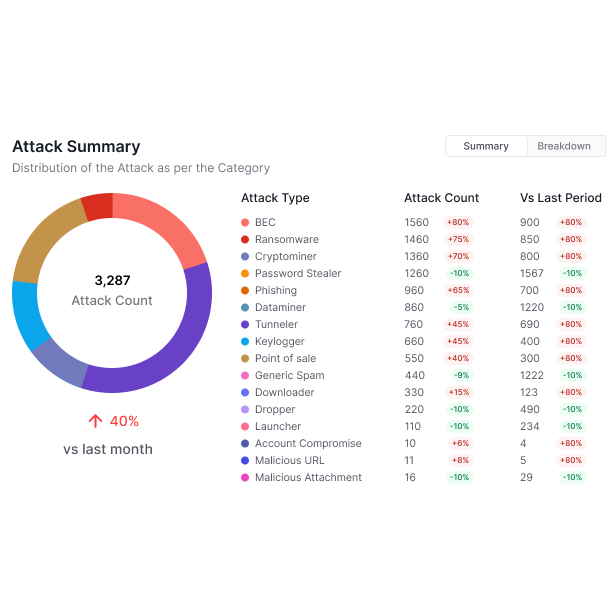
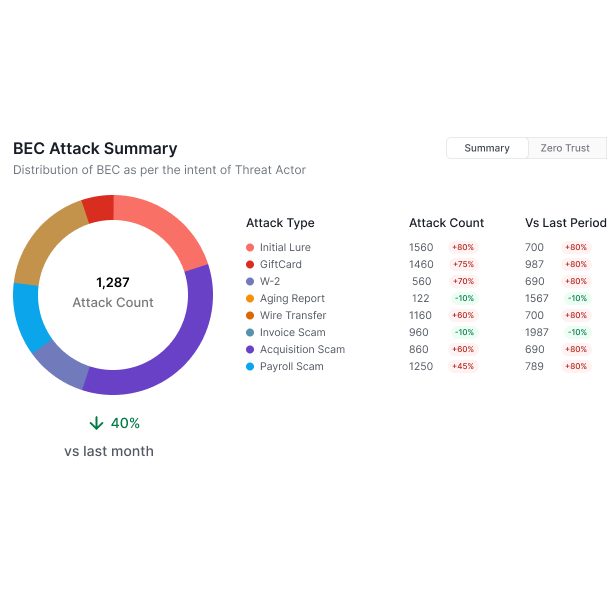
Legacy detection technologies (signature based, sandboxes, endpoint security, etc.) rely on finding and classifying a malicious payload to stop threats.
Attackers continuously evade these technologies easily, leading to ransomware impacting 1 in 10 organizations, and a 341% yearly increase in phishing.
Traditional Business Email Compromise (BEC) detection requires a baseline analysis of VIP employee behavior.
This approach lacks the scalability and performance to monitor every employee, and is immune to current BEC tactics which target everyone in the organization.
New AI, purpose-built to craft evasive malicious payload, is exponentially changing the scale, precision, and variance of attack delivery, overwhelming existing technologies.
Attacks are instantly iterated with AI to generate variations that bypass sandboxes, scanners, pre-trained classifiers, and human scrutiny.



Attackers prey on employee strengths, exploiting responsiveness, speed, trust, and work ethic to take advantage of easy targets.
Relying on employees as a last line of defense is inefficient, unfair and increasingly ineffective against AI-built attacks.










of evasive attacks bypass traditional defenses
More phishing & malware detected
by NACETM
in 50 employees exposed to advanced email threats/month
or fewer
false positives
per month
Never Ending Evasive Attacks Hide Payloads to Evade Existing Tools
NACETM takes a first principles approach, making decisions without relying on malicious payloads—whether from threat actors or AI—making it completely immune to evasions.
Malicious URLs bypass Sandboxes, Reputation, Domain analysis and Reach Inboxes Daily
NACETM leverages Generative and Predictive AI to understand the intent of an email, whether authored by a threat actor or AI, and uses contextual relationships between the intent, SMTP headers, and auxiliary information from URLs to derive a verdict
Malicious AI makes impersonating employees easier and more lucrative than ever before
NACETM Intent Analysis uses a patent pending. multimodal, semantic-aware approach to stop BEC by understanding topics, tone, sentiment, and tactics, and via zero-trust validation.
Intent Analysis means that NACETM is as good at stopping threats as it is at allowing true business communication. False positives are typically as low as 3-5 messages/month, well inside any team's ability to investigate.
New evasion methods create opportunities for exploitation, leaving employees as the last line of defense against sophisticated phishing and ransomware attacks. NACETM stands apart by eliminating the reliance on malicious payloads in its decision-making process, making it inherently immune to evasions crafted by threat actors or AI, ensuring unwavering and robust protection against new evasions and 0-day threats.
NACETM is built on a modern, scalable cloud-native platform that has well understood costs, and highly efficient engines. We are so confident in our ability to catch what others can't, that we don't charge unless we prove our worth.
Whether you're looking to add defense in depth, replace a legacy secure email gateway, or just see whether employee behavior-based tools are actually as good as they promise, we welcome every chance to go head-to-head with the previous generations of email security.
See what evasive threats are slipping through your defenses with our free assessment.
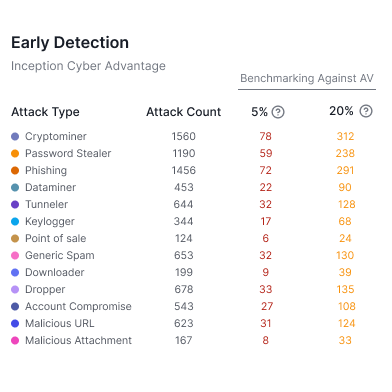
Stopping more threats, saving SOC analysis time, and eliminating remediation effort
Inception Cyber added value immediately. It was deployed in less than 10 minutes, and within the first 5 days of deployment their Intent-Based AI approach caught and stopped a number of BEC, phishing and malware threats—including an extremely sophisticated HTML smuggling attack purpose-built to smuggle malware through other security tools. The product's AI-driven decision explanations are impressive and will be invaluable for both analysts and employees.

Ritesh Jain
SVP-Enterprise Security Business at Doyen InfosolutionsWe are using your email security solution for couple of months now. Inception Cyber’s intent-based approach delivers unmatched precision in detecting evasive BEC and phishing emails, stopping threats that evade traditional defenses.

Manoj Kumar
IT/CIO at Ambica SteelsThank you for presenting your research, 'Harnessing Large Language Models for
Detecting Malicious Attachments' at AVAR 2024. It was well received by the audience and the feedback about the content has been overwhelmingly positive. Please continue sharing your research with the cyber security community, I look forward to similar contributions from you at AVAR 2025.

Kesavardhanan Jayaraman
CEO, AVAR - Association of Anti-Virus Asia ResearchersInception Cyber has proven its effectiveness in live deployment, by analyzing tens of millions of emails to consistently detect evasive threats—including phishing, malicious attachments, and business email compromise (BEC)—that other technologies miss. By focusing on intent as a core feature in its decision-making process, rather than relying on indicators from the exploitation stage or user behavior, Inception delivers proactive protection and identifies hard-to-find threats. This approach safeguards every employee—not just high-profile targets—against highly targeted campaigns tailored to our organization, people, and brand.
Head of Technology
US Financial InstitutionI’ve worked in cybersecurity for over 20 years and manage security services for many customers. Inception Cyber is now my top-tier email security solution, and the one I also trust to protect my own business. Deployment took less than 10 minutes, and the team has been immediate and thorough in their support, which gave me the confidence to roll it out widely. What really sealed it was seeing the types of threats stopped that slipped past other tools, including a leading secure web gateway—things like spoofed emails that looked like they came from me, fraudulent payment scams, and internal phishing attempts disguised as payroll/bonus messages. Inception Cyber caught them all.
Lucas Wellman
Founder and Technology Success Executive, Status ProsWithin days of deployment, InceptionCyber.ai’s intent-based threat prevention platform uncovered highly targeted BEC, investment-fraud campaigns that had bypassed our existing security controls and reached our users’ inboxes. Beyond stopping these high-risk threats, it also helped us identify and reduce ‘grey’ and spam emails that were impacting employee productivity.
CISO
Large Nonprofit Healthcare InstitutionLearn more about how Inception Cyber is revolutionizing the way to prevent the evasive threats of today, and the future.





